Import a serial signing key¶
Note
This option for generating serial signing keys is not recommended. We suggest creating your serial signing keys in the Serial Vault so that the private keys are never available externally, reducing the attack surface. For instructions, please see Generate a serial signing key .
Generating a serial signing key locally¶
To proceed, you need to generate a signing key as the Brand Account. This will be uploaded to the Serial Vault and used to sign Serial Assertions. The key must abide by the following conditions:
This key must be generated and registered as the Brand Account
This key must be passwordless
Note
Generating the key takes some time. Moving the mouse or typing can help to speed up the process, as does installing the rng-tools Debian package beforehand.
Ensure you do not enter a passphrase for this key when prompted. This special key is used exclusively for providing devices access to the store and must be passwordless. When prompted in the terminal, or if a pop-up displays, do not enter text as a Passphrase and do not enter text to Confirm it. If you do, this key will not function to sign Serial Assertions.
$ snapcraft create-key serial
Passphrase: # must be a passwordless key, so press Enter twice
Confirm passphrase:
[ . . . ]
Register a serial signing key¶
Register the serial key with the following command:
$ snapcraft register-key serial
[ . . . ]
When prompted, enter the credentials for the Brand Account.
Note
The key does not function if another account is specified. This is by design in order to ensure the Brand Account’s scope of authority.
Verify the serial key exists¶
Use snapcraft list-keys to verify a key named serial exists:
$ snapcraft list-keys
Name SHA3-384 fingerprint
* serial <fingerprint>
Armor the serial key¶
Export the serial key as an armored file so that it can be safely uploaded to the Serial Vault, as follows:
$ gpg --homedir ~/.snap/gnupg --armor --export-secret-key serial > serial.asc
You should now have a serial.asc file registered that can be imported to the Serial Vault.
Uploading the key to the Serial Vault¶
The ASCII-armored file can be uploaded to the Serial Vault. To import the serial signing key, Log in to the Serial Vault with the Administrator account. Select the Signing Keys section at the top, and click the ![]() button to import a signing key. Note that the Serial Vault cannot be logged in via the Brand Account.
button to import a signing key. Note that the Serial Vault cannot be logged in via the Brand Account.
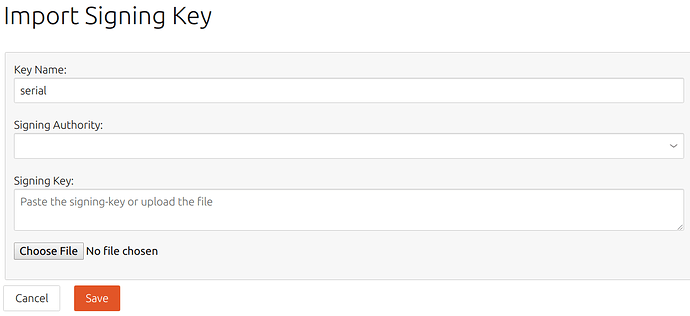
Enter serial in the Key Name field as shown in the screenshot above.
In the Signing Authority field, select the account ID of the Brand Account. This is the same value as the developer-id displayed by snapcraft whoami when you are logged into snapcraft as the Brand Account.
Click Choose File, and browse to and select the serial.asc file on your local system as created above.
Click Save to complete the upload.
Backing up and protecting keys¶
The signing keys that have been generated are an essential part of verifying the authenticity of a device at the Dedicated Snap Store. So these keys need to be protected and backed up. They are stored by default in ~/.snap/gnupg on the current machine.
Whilst the Serial Vault does hold the private key (encrypted in the database), it does not provide a mechanism to download a signing key. The Dedicated Snap Store only has the public part of the key. So it is important to ensure that the generated keys are backed up.
